
VulSync
VulSync is an innovative reporting platform developed in-house by Safe Decision to revolutionize vulnerability assessments and penetration testing engagements for our clients. Traditionally, vulnerability assessment and penetration testing (VAPT) services often involve lengthy waiting periods for clients to receive findings reports and begin the mitigation efforts. VulSync changes the game by providing real-time updates on project status and vulnerabilities discovered, empowering clients to take immediate action to mitigate risks.
FEATURES
VulSync Reporting Platform

FEATURES
Key Features

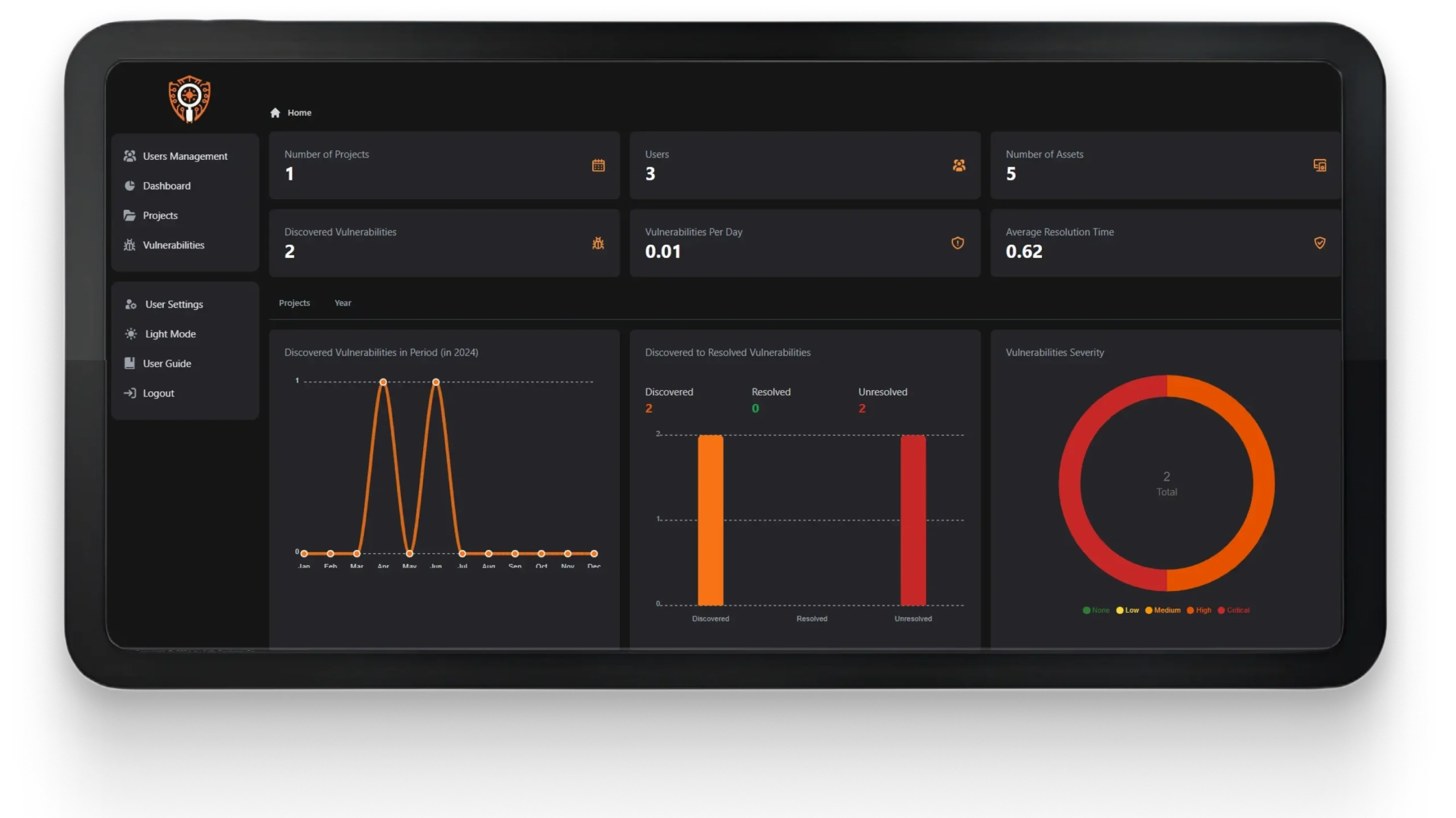
Real Time Reporting
With VulSync, clients gain access to real-time updates on project status and vulnerabilities as they are uncovered by our penetration testing team. Say goodbye to waiting weeks or months for findings reports – VulSync delivers information instantly.

Comprehensive Vulnerability Details
VulSync provides detailed information on vulnerabilities discovered during the VAPT engagement, including descriptions, proof-of-concepts (POCs), severity levels, and recommended mitigation strategies. Clients have all the information they need to prioritize and address vulnerabilities effectively.

Interactive Dashboard
Our user-friendly dashboard allows clients to easily navigate and track the progress of their VAPT engagement. From viewing project status to accessing detailed vulnerability reports, VulSync puts all the information at your fingertips.

Effortless Collaboration
VulSync facilitates seamless collaboration between our penetration testing team and clients. Clients can add comments, request validation testing of fixed vulnerabilities, and engage in ongoing discussions with our experts, streamlining the vulnerability management process.

Customized Reporting
With VulSync, clients can generate customized reports tailored to their specific needs and requirements. Whether it's executive summaries or detailed technical reports, VulSync ensures that clients receive the insights they need to make informed decisions.
Platform
Streamlined Vulnerability Management
VulSync simplifies the vulnerability management process by providing a centralized platform for tracking, prioritizing, and mitigating vulnerabilities. Clients can efficiently manage their security posture without the hassle of manual reporting processes and long waiting periods.

FAQ's
Have a Question?
We’ve got this!
What frameworks and standards does Safe Decision align with?
What is included in your Managed Security Controls service?
Do you offer cloud security assessments for hybrid environments?
Does Safe Decision offer proactive threat hunting services?
Do you offer penetration testing with full reporting aligned with MITRE ATT&CK?
What capabilities does the Safe Compliance platform offer?
What detection technologies are used in your Safe SOC service?
Do you offer secure private cloud hosting within Saudi Arabia?

Get in touch with us!
Fill out the form and let’s talk how to make your business secured!
- Experts in cybersecurity
- 12+ years of securing businesses
- We bring continuous innovation and Improvement to your business
















